Based on your feedback, we recently enabled public registration on our Git service to enable collaboration. After a month of public registrations and disproportionate abuse, we regrettably had to disable it again. Registration will remain available only to Single Sign-On clients for now.
What happened?
On November 6th, we observed high error rates on our mailserver. Around 80% of our emails were not deliverable, which is a potential indicator of abuse. It also risks our deliverability of other emails to you, due to the mailserver being marked as problematic.
Upon investigation, the origin for the high error rate were registration emails for our Git service. Accounts were being created for emails that did not exist. Specifically, between October 9th and November 6th, 27 spam accounts were created that were never activated or used beyond that point. In comparison, we received no legitimate public registrations. We observed no abusive behavior on the service as a result of the spam accounts, and all spam accounts have been removed.
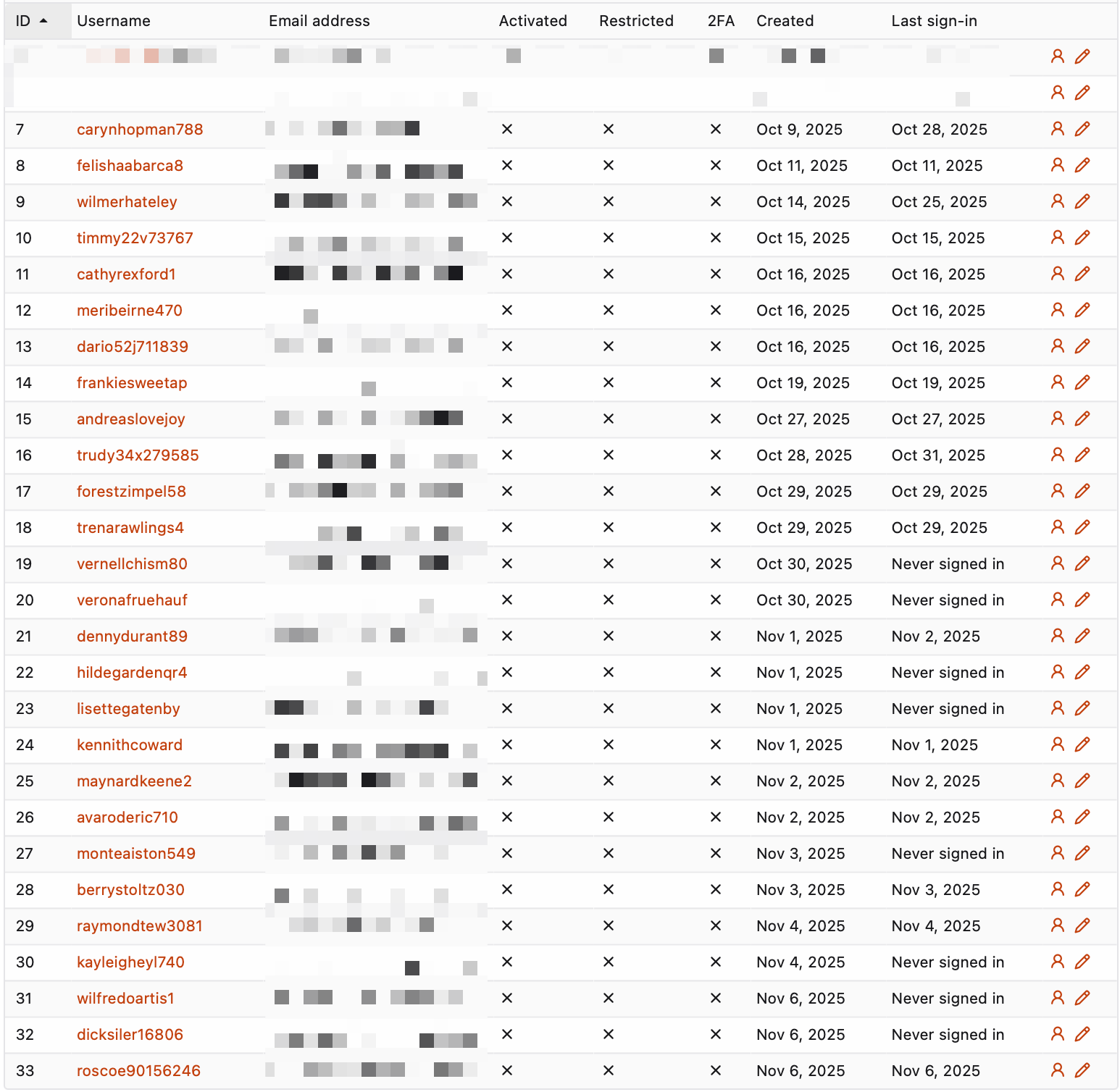
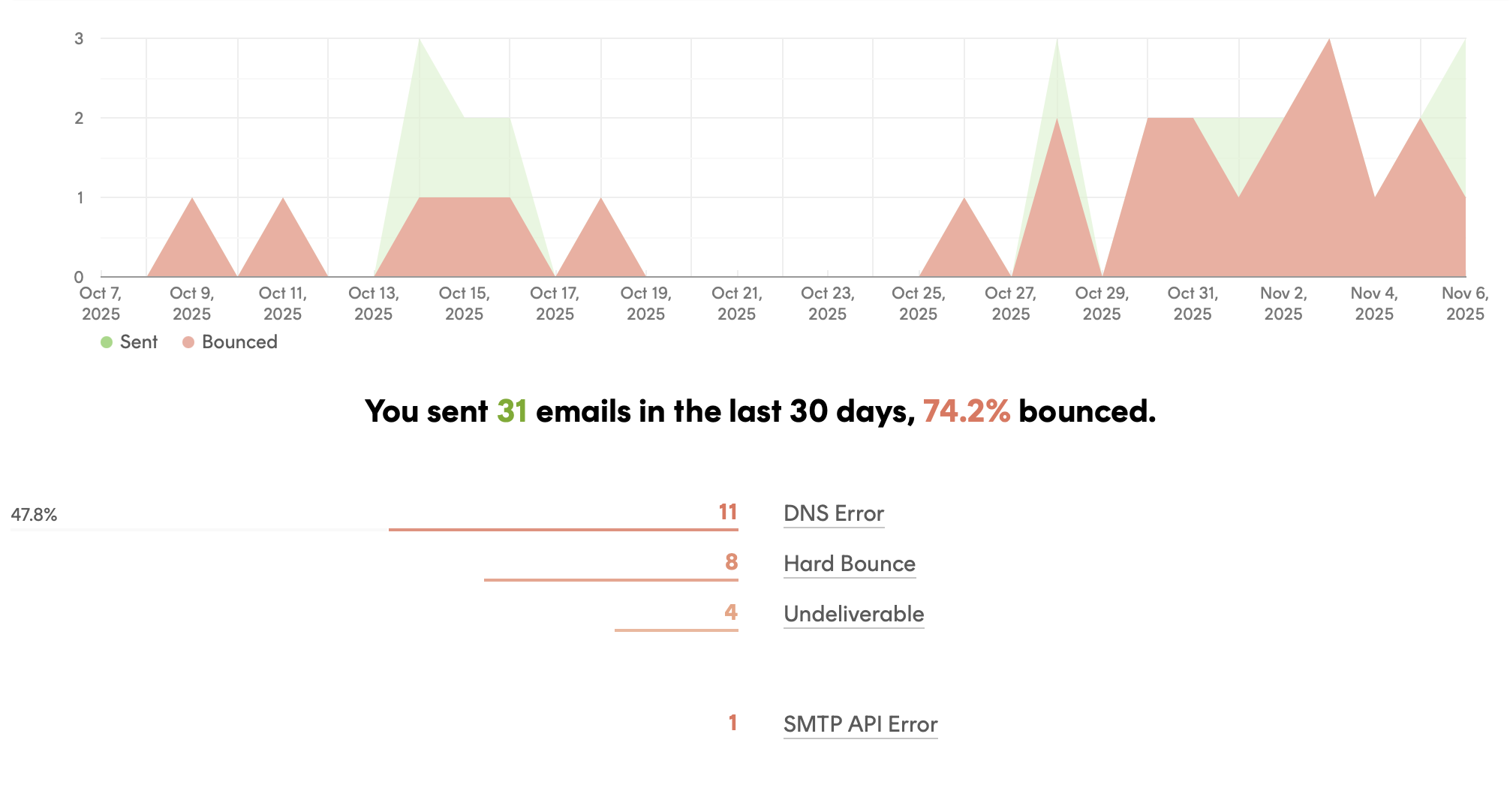
Left: Screenshot of the registration table, indicating the vast amount of spam accounts compared to legitimate ones. All personal information, including those of spam accounts, have been blurred out. Right: Screenshot of the mailserver statistics, indicating a bounce rate of 74.2%.
For our own documentation, here are the domain names that were included as part of the registrations:
@730e.dynamictelegraph.website
@discard.email (2x)
@e327.visionsofpeace.website (2x)
@gmail.com (8x)
@lightraygrowthsolutions.com
@mailmenot.io (11x)
@pertomail.top
@spambog.com
Listing of email domains used to register spam accounts.
What led to this?
When we enabled public user registrations on the Git service, we made sure that public registrations could only leave comments and create forks. They would not be able to create their own repositories. This mitigated abusive behavior after completing the registration, but public registration was the root cause.
Our Git service runs on Forgejo, which is deployed by many people and organizations on the web. The largest instance Codeberg, who have seen various instances of abuse and spam over the years. With the popularity of Forgejo as a Git service, the attack vector gets standardized for all services using this software. We expect this is how the abuse happened: Our Git service was identified as running Forgejo, and the abuser(s) started creating accounts in the hopes of uploading malware or illegal materials.
What are we doing differently moving forward?
First, we disabled public registrations. We realize this makes it harder for you to collaborate. We also recognize that our Git service is still a very small part of our operations. We cannot moderate public registrations that outweigh legitimate registrations by a factor of ten.
Second, we are revisiting our monitoring frequency. Our mailserver provided reliable indication for abuse. Once observed, we were able to quickly take action on that information and eliminate the root cause. As a result, we will monitor our mailservers on a weekly schedule instead of a more sporadic schedule.
We appreciate your trust in hosting your Git repositories on our service. We understand the current situation is not ideal and we are trying to address this in a reasonable manner.
We are grateful for any further questions or feedback in a reply, or more publicly on our feedback forum. These decisions are not intended to be permanent. With your help we can continue the conversations around access, security, and how we offer these services in a way that works for all of us.


